Unfortunately, there are times where monitoring software isn’t welcomed or appreciated. Hackers, snoopers, or overreaching IT admins can all push the boundaries too far. If you’re worried about your privacy, you can learn to detect computer and email monitoring or spying software by following these steps.
Monitoring at Home, School, or Work
Before you begin to look at how to detect certain types of computer and email monitoring, you may need to determine your rights. As an employee, your rights to unfiltered access to the web, email, or general PC usage could be much lower, although that doesn’t mean that there aren’t boundaries that can’t be crossed. You may not own the equipment, and depending on your contract, your employer or school may hold the right to log any data on your PC usage. While there are ways to monitor this, you might not be able to stop or work around it. The same applies in an educational setting, where strict controls on PC and web usage are likely. It’s a different scenario entirely for a personal PC on a home network, however. Your PC, your rules – unless it isn’t your equipment. Parents, for instance, may place monitoring software to keep their children safe, but so too may abusive partners, or malicious hackers thousands of miles away. Whether it’s at home, school, or at the office, there are a number of ways you can check for the typical kind of computer or email monitoring that can take place.
Checking for Email Monitoring Software
If you want to check for email monitoring, consider first whether you’re using a personal, corporate, or educational email account. For corporate or educational accounts, a system administrator likely has the power to access your emails at any point, with all emails routed through a secure server that they may also control. If that’s the case, you should always assume that your emails are monitored in some way. It might be actively monitored, where each email is checked and logged, or the monitoring could be less specific, with information on when you send and receive emails (as well as the recipients or senders) logged separately. Even with less active monitoring, an administrator over a corporate or educational email account can still reset your password to access your emails at any point.
Checking Email Headers
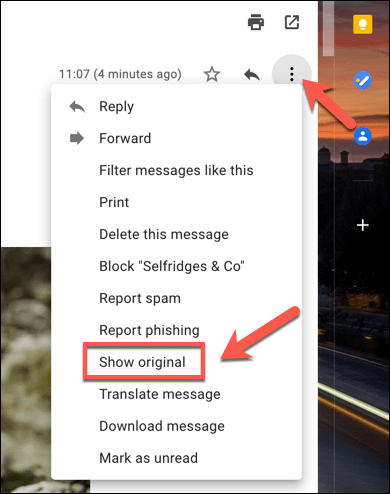
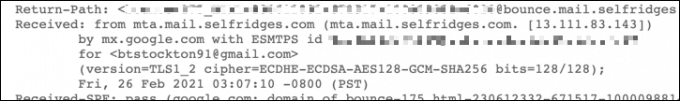
You can usually determine if your emails are being routed through a corporate email server by looking at the headers for emails you receive. For instance, in Gmail, you can look up the headers by opening an email and selecting the three-dots menu icon in the top-right. From the options, select the Show Original option. Looking at the headers, the Received header will show where the email originated from and the email server being used. If the email is routed through a corporate server or is scanned by a filter, you can assume that the email is being (or can be) logged and monitored.
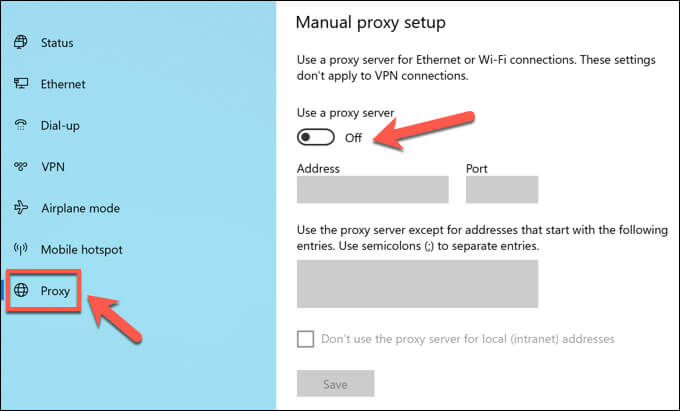
Using Proxy Servers
If you’re using a desktop email client like Microsoft Outlook, it’s possible that your emails are being monitored through a proxy server. A proxy server can be used to log certain data, as well as forward it to other servers. You can check your proxy settings on Windows 10 in the Windows Settings menu (if you have access to this). It’s also possible that your Outlook mailbox settings are designed to route through an email server over a specific proxy. This is set up when your account mailbox is added to Outlook which, for corporate devices, is likely configured for you automatically. Unfortunately, the only way to test this (without administrator access yourself) is to send and receive emails between a personal account and an account you suspect is monitored. Monitoring the email headers, you may be able to spot if a proxy server is used using the Received or X-Forwarded-For headers.
Checking for Monitoring Software
A more typical method of digital monitoring is through software installed on your PC, tracking your web activity, the software you use, and even your microphone, webcam, and keyboard usage. Almost everything you do on your PC is loggable with the right software. Looking for the signs that you’re being monitored, however, can be a little harder. There isn’t always a handy icon in the Windows taskbar to look for, so you’ll need to dig a little deeper.
Checking Windows Task Manager
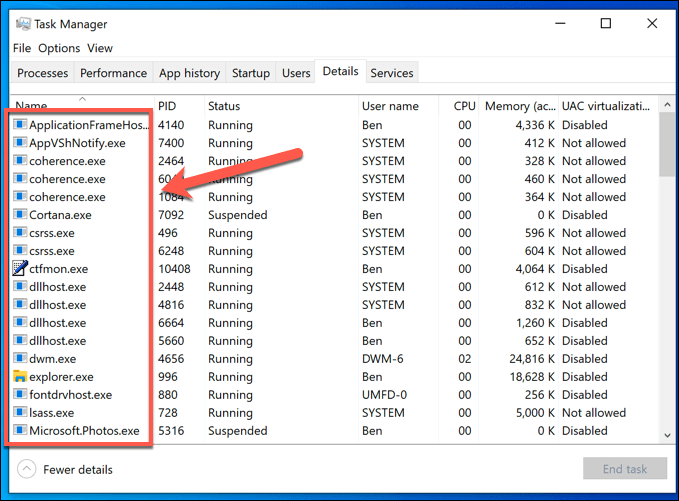
If you suspect there’s software on your Windows PC that’s recording your activity, you might want to check your list of running processes first using Task Manager. There is where you’ll find a list of all the running software on your PC. Running processes with non-descript names should raise your suspicions (although not always). While it may prove time consuming, you should use a search engine to investigate each running process in turn. For instance, ntoskrnl.exe is a perfectly legitimate (and essential) Windows process. If you spotted student.exe (the monitoring app for the LanSchool monitoring service for schools) in the list, however, you can assume you’re being monitored. You should also look for common remote desktop connection software, such as VNC, LogMeIn, or TeamViewer. These screen sharing apps allow a remote user to take control of your PC, giving them the ability to open apps, perform tasks, record your screen usage, and more. Windows also has its own remote desktop service, allowing other Windows PCs to view and control your PC. The good news is that RDP connections typically only allow one person to view a screen at the same time. As long as you’re logged in, another user shouldn’t be able to view or control your PC.
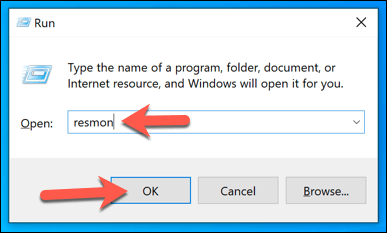
Looking at Active Network Connections
The process manager is a good way to check for active monitoring software, but this only works if the software is currently active. In certain settings (such as a school environment), you may not have permission to open the Task Manager to look in the first place. Most logging software usually works by recording data locally and sending it to a server or administrator elsewhere. This could be locally (on your own network) or to an internet-based server. To do this, you’ll need to look at the active network connections on your PC. One way to do this is to use the built-in Resource Monitor. This little-known Windows app allows you to view any active communications, both ingoing and outgoing, from your PC. It’s also an app that often remains available on corporate and educational PCs. Any connections to other devices in reserved IP ranges (eg. 10.0.0.1 to 10.255.255.255 or 192.168.0.1 to 192.168.255.255) means data is being shared over your network, but connections to other ranges points to an internet-based administration server. You may need to research some of the processes listed here to identify possible apps. For instance, if you spot a process that you don’t recognize with a number of active connections, sending and receiving a lot of data, or using an uncommon port (typically a 5-digit number), use a search engine to research it further.
Spotting Keyboard, Webcam, and Microphone Logging
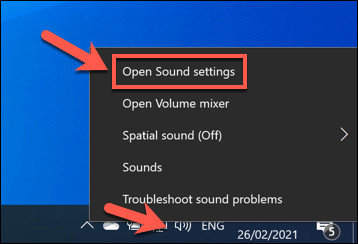
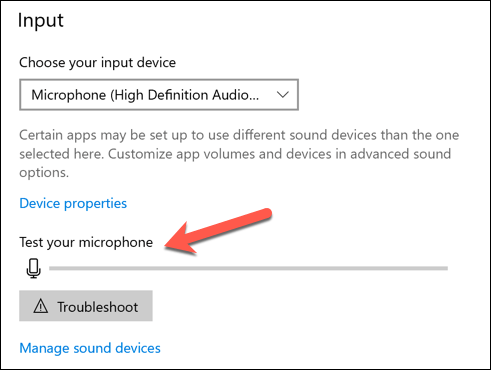
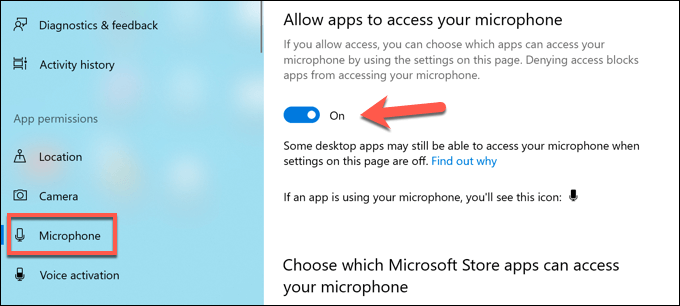
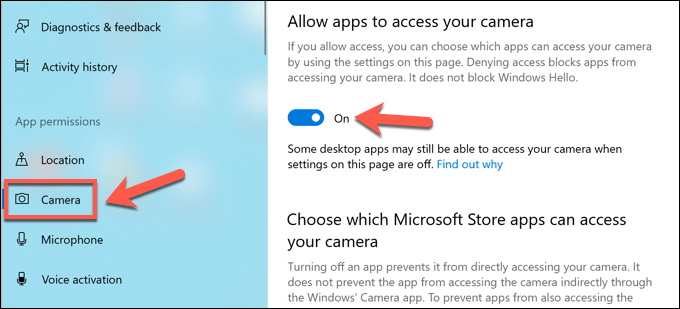
PC monitoring software isn’t just about recording your web usage—it can prove to be a lot more personal. Where possible, apps like these can (and may) monitor your webcam and monitor usage, or record all active keypresses you make. Everything you type, say, or do on your PC could be recorded and examined later. If this is happening, you’ll need to try and spot the signs. Most built-in and external webcams display a light (usually a green or white LED) to show that a webcam is active. Microphone usage is trickier to spot, but you can check what sounds a microphone is detecting in the Sound settings menu. If you have permissions to do so, you can block access to your mic or camera in the Windows Settings menu. The steps above should help you to limit what somebody can see or hear, but you may need to take additional steps to block keylogging attempts.
Protecting Against Government Monitoring
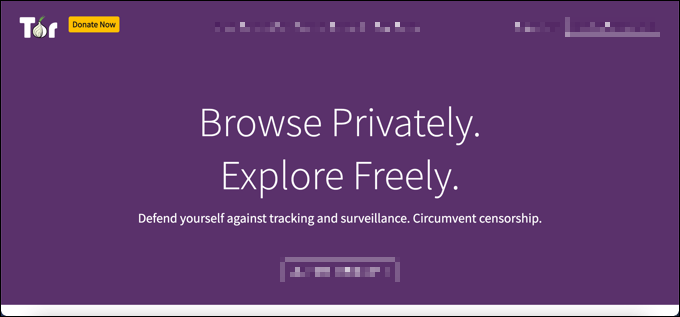
The methods we’ve outlined above work well to spot the kind of monitoring you can expect at home or at work, but they’re less likely to work to spot government monitoring. In certain areas of the world, your digital activity is likely to be recorded and censored. Protecting against this kind of computer monitoring online can be difficult, but it isn’t impossible. Some of the best virtual private networks can work in areas of the world where internet censorship is common, but you can also use Tor to bypass restrictions and protect your privacy instead. Unfortunately, the only way to truly prevent government agents from monitoring your digital usage is to switch to encrypted platforms for communication. A number of encrypted chat platforms exist, such as Signal, that support end-to-end encryption, allowing you to chat freely without fear of censorship.
Protect Yourself Against Snoopers
As the steps above show, there are a number of ways that corporate administrators, overbearing parents, disgruntled exes, malicious hackers, and even government spies can monitor your PC usage. This isn’t always something you can control, especially if you’re an employee using a corporate network. If you’re using a personal PC, however, there are steps you can take to protect your PC. Using a virtual private network is a great way to hide your internet usage, but it can also block outgoing attempts to connect to your PC. You could also think about beefing up your PC with a third-party firewall to stop unnecessary access. If you’re really worried about your network security, you can look at other ways to isolate your PC usage. You could switch to a Linux distribution, offering more security than a typical Windows PC. If you want to turn white-hat, you can even think about a Linux distro for hacking, allowing you to test your network for security holes.